As we navigate our way into an increasingly digital realm, the Internet of Things continues to revolutionize how we monitor our environments, control our surroundings, and increase efficiency in everyday life. As our reliance on IoT grows, so does our need for secure communication. Let’s look into the possible design of a secure IoT application using a Virtual Private Network (VPN).
How is My Data Being Routed?
When designing the security implementations of an IoT application, is it essential to know how data is being routed. Understanding the journey of your data helps you craft an IoT security strategy that can effectively safeguard your data.
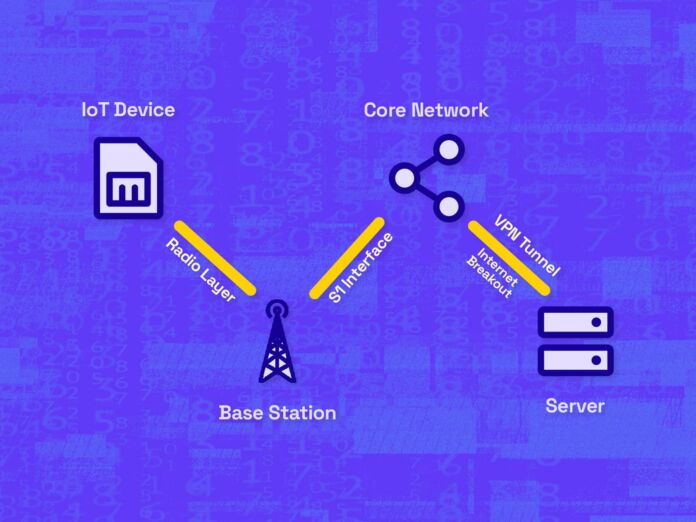
IoT data typically originates from a device, travels to a base station, then onto the core network of a Mobile (Virtual) Network Operator. Finally, data is routed to a server endpoint for storage and processing.
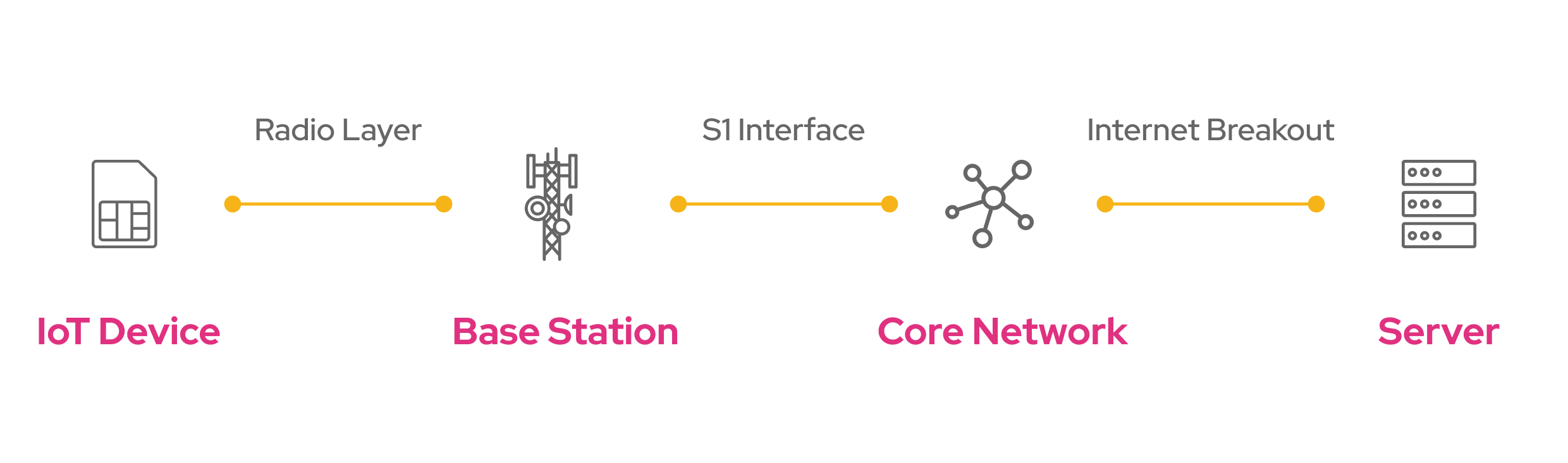
IoT Device: Communication is often initiated from the end device which spends most of its life in deep-sleep mode to conserve energy. It only wakes up to inform the server about its latest sensor readings or state changes. These devices have a cellular module and a SIM card to authenticate and connect with the cellular network. The device transmits data over the air which is referred to as the radio layer.
Base Station: Devices connect to a specific cell tower, also known as a base station. Base stations demodulate the radio signals and send data over the so-called S1 Interface to the core network of the device’s mobile operator. Base stations review the device’s APN configurations to determine the destination of the data.
Core Network: The core network is responsible for handling functions like user authentication, mobility management, and IP (Internet Protocol) address assignment. It also routes data to its intended destination via the public Internet.
Server: The ultimate destination: the server. The server could be a cloud-based platform or an on-premises private server, for example, hosted in a trusted AWS or Azure domain. Here, the data is stored, processed, and analyzed.
VPNs in IoT
Let’s dive into the role of VPNs in IoT security.
Think of an IoT data packet as a postcard traveling through a mail system. Just like a postcard, data sent over the internet is visible to anyone handling the message if not properly secured. A VPN acts like an envelope, providing a secure wrapper around the message to hide the contents and ensuring that it can’t be read while in transit as it uses private mailboxes inaccessible to the public.
Although VPN clients can be installed on the end device directly, VPNs are commonly used to secure traffic from the core network, up to a private server. This secure connection between two endpoints is what is called a VPN tunnel.
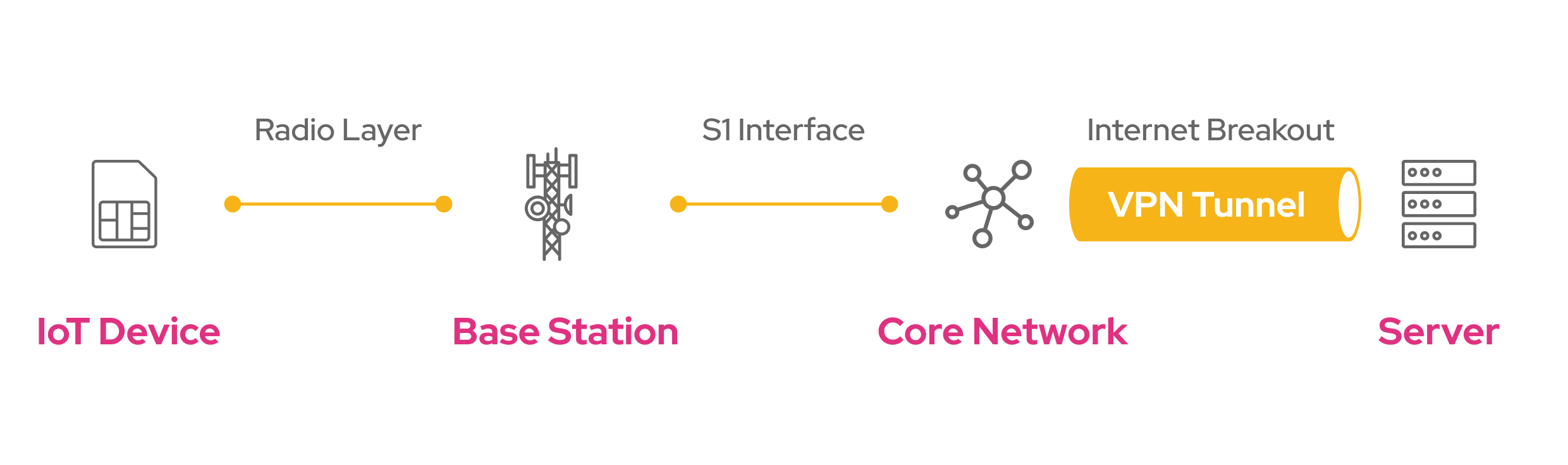
Secure Tunnel
The VPN tunnel is created to connect two IP endpoints, e.g. the Core Network and a private server running in AWS or Azure. This secure tunnel allows data to be transferred through the public internet, without intermediate parties being able to read what’s sent through it. Imagine each data packet being encapsulated in a new message which hides the content of the original message and can only be delivered to one specific postbox. Once delivered at the end of the tunnel (the private server), the data gets decapsulated and the original message is delivered.
Hidden IP address
The encapsulation of the original message not only hides the content of the message but also masks the IP addresses of the original sender and receiver. If the message would get intercepted, only the IP addresses of the VPN tunnel’s endpoints would be shown, not the actual ones.
Additional Encryption
A nice add-on that comes with all VPN services is the additional layer of encryption. VPNs not only create a tunnel between two endpoints, but they also encrypt the payload to further protect their content (for example using the IPSec protocol).
Required Level of Security
Not all data is equal. Some data is highly sensitive, such as personally identifiable information or healthcare data, and requires robust security measures. Other data might be less sensitive but still requires protection to ensure data integrity and authenticity.
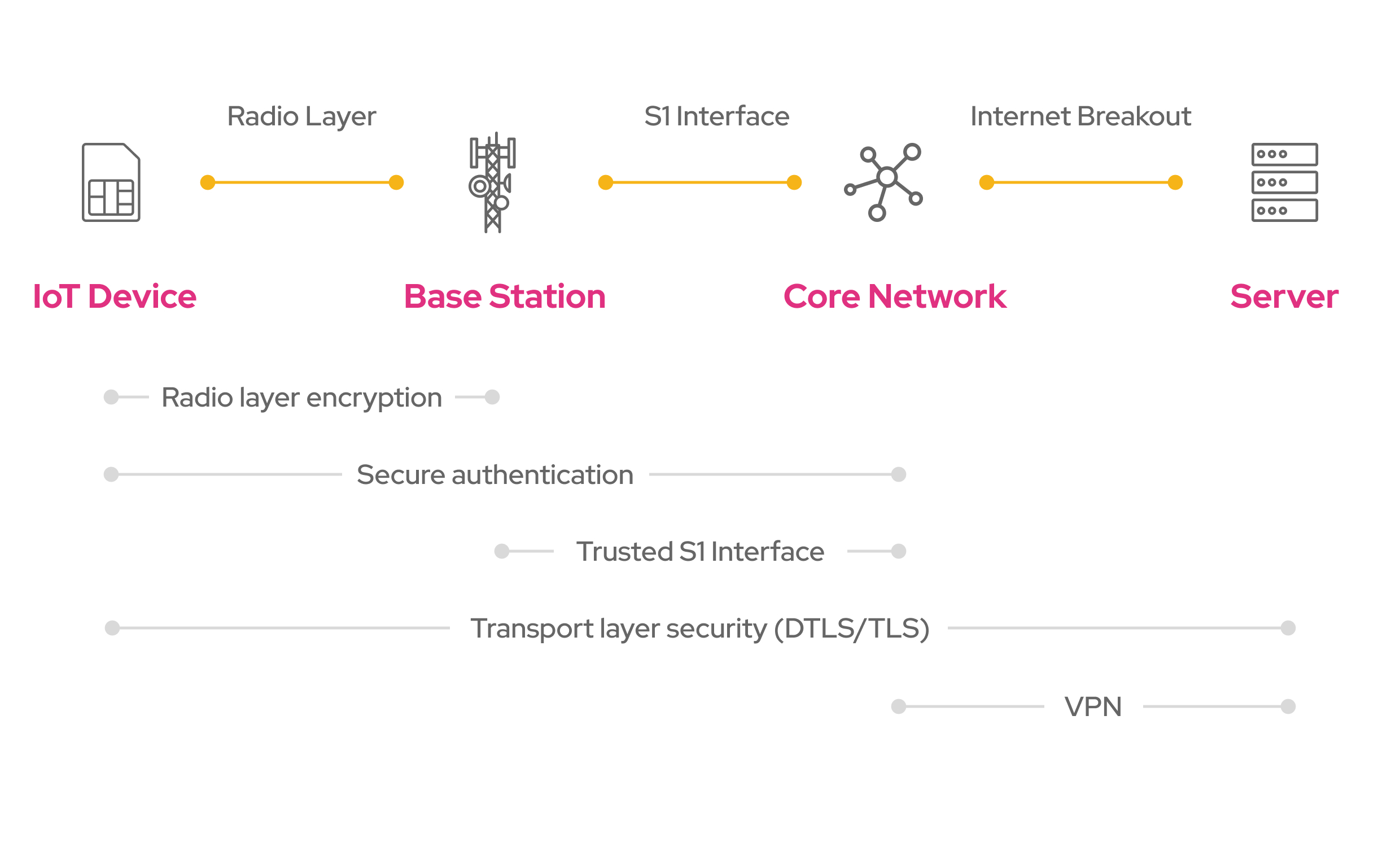
When designing the architecture of an IoT application, security needs to be designed from the device, up to the server. Depending on the security needs, one or multiple redundant layers of protection can be implemented. This multi-layered approach – known as defense in depth – ensures ongoing protection even if one layer is compromised.
By default, cellular communication is secure from the IoT device up to the core network as per 3GPP standards. This includes authentication (verifying the device’s identity using AKA or EPS-AKA), radio layer encryption (protecting the data sent over radio waves using EEA algorithms), and a trusted S1 Interface (often using a method called IPSec).
In addition, to ensure end-to-end security, many IoT applications adopt security protocols like DTLS or TLS which secure data traffic between the IoT device and the server.
Now, where do VPNs fit into this IoT architecture? VPNs are often used as an additional security layer, though sometimes VPNs are used instead of DTLS/TLS as data is already secured from the device up to the core network.
The design of your IoT application highly depends on the required level of security. Strategies like defense in depth can significantly enhance the security of IoT applications. However, more complex implementations may demand more resources and add complexity to the IoT solution as a whole.
Tweet
Share
Share
- Cloud Software
- Cybersecurity
- Network and Protocols
- Privacy
- Security
- Cloud Software
- Cybersecurity
- Network and Protocols
- Privacy
- Security
